Navigating the Final Phase of NIS2 Directive Compliance
Michael Solon Kassinis 12:11 - 10 September 2024

In the rapidly evolving landscape of cyber threats, the European Union has taken a bold step to enhance cybersecurity and safeguard its digital infrastructure with the introduction of the Network and Information Security Directive (NIS2). This new directive aims to create a robust cybersecurity framework, addressing the urgent need for stronger defences in an era where cyberattacks have surged dramatically.
Unlike its predecessor, NIS1, the enhanced NIS2 directive covers a broader range of entities and enforces more stringent security requirements. It not only focuses on vital organisations within the EU but also includes external entities doing business with the EU, ensuring comprehensive protection and resilience.
NIS2 will impact sectors deemed essential for a functioning society. These sectors are divided into two main categories: "Highly-Critical" and "Other-Critical."
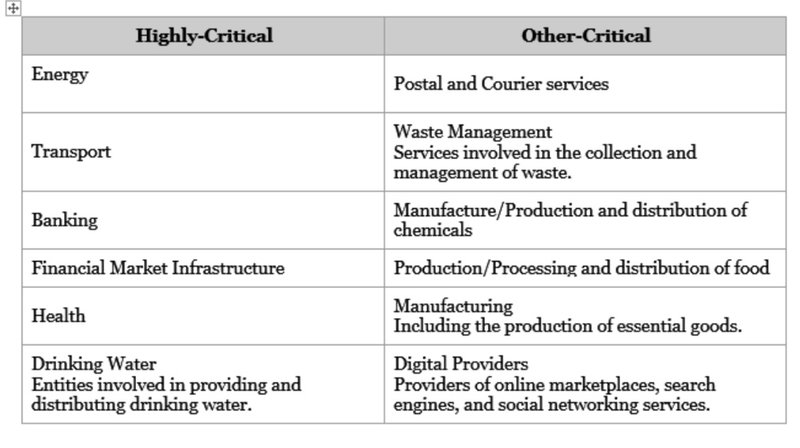
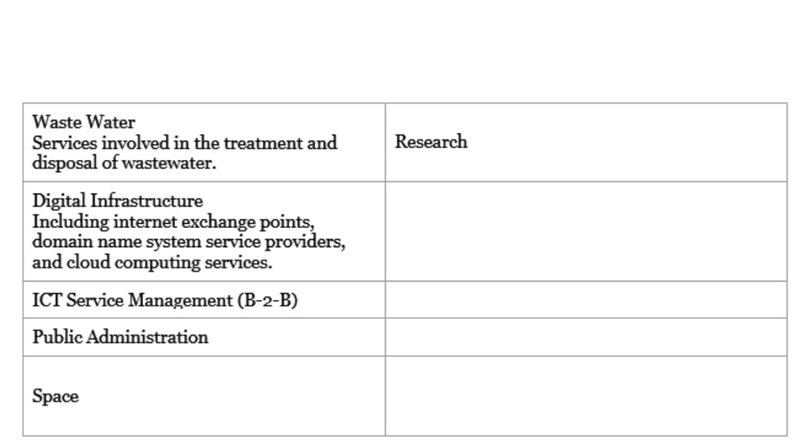
Additionally, the directive introduces a new classification level: "Essential" and "Important" entities. This classification determines how organisations must meet security requirements and how they will be supervised and penalised for non-compliance. An organisation is considered "Essential" if it belongs to a highly critical sector and exceeds the ceilings for medium-sized enterprises (The category of micro, small and medium-sized enterprises (SMEs) is made up of enterprises which employ fewer than 250 people and which have an annual turnover not exceeding EUR 50 million, and/or an annual balance sheet total not exceeding EUR 43 million). NIS2 mandates an all-hazards approach to safeguard network and information systems and their physical environments. Measures include:
● Policies on risk analysis and information system security
● Incident handling
● Business continuity, such as backup management and disaster recovery, and crisis management
● Supply chain security, including security-related aspects concerning the relationships between each entity and its direct suppliers or service providers
● Security in network and information systems acquisition, development, and maintenance, including vulnerability handling and disclosure
● Policies and procedures to assess the effectiveness of cybersecurity risk-management measures
● Basic cyber hygiene practices and cybersecurity training
● Policies and procedures regarding the use of cryptography and, where appropriate, encryption
● Human resources security, access control policies, and asset management
● The use of multi-factor authentication or continuous authentication solutions, secured voice, video and text communications, and secured emergency communication systems within the entity, where appropriate
The directive also introduces new reporting obligations in case of significant incidents. Entities are required to inform the national CSIRT or, where applicable, the competent authority. An early warning should indicate whether the significant incident is suspected of being caused by unlawful or malicious acts or could have a cross-border impact.
Organisations should also anticipate regular audits, security scans, on-site and off-site inspections, and data/documentation requests. The NIS2 Directive represents a significant shift from the more voluntary approach of its predecessor and non-compliance can result in penalties such as compliance orders and binding instructions, criminal sanctions for management, and financial penalties, akin to those under the GDPR, on organisations that fail to comply within the specified timeframe.
Essential entities face fines up to at least 10 million euros or 2% of total worldwide annual turnover, whichever is higher. Important entities face fines up to at least 7 million euros or 1.4% of total worldwide annual turnover, whichever is higher.
Notably, there are also potential repercussions for C-level executives of non-compliant organisations, including possible restrictions on their positions across executive boards. To prepare for NIS2, organisations can take the following steps:
● Determine the need to comply with the directive
● Perform a risk assessment to identify security gaps
● Put in place the necessary security measures
● Verify the security compliance of suppliers
● Test and evaluate the measures to ensure they work as intended and make changes where necessary
● Promote security awareness among employees
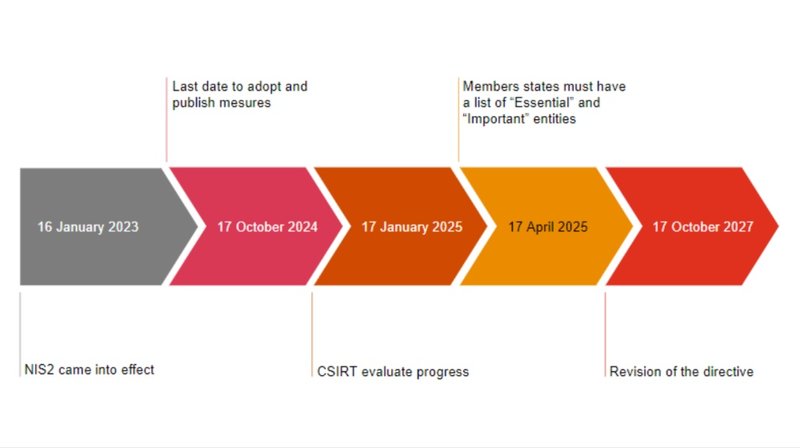
The NIS2 directive is set to come into effect on October 17, 2024, with less than four months to prepare. This regulation represents a significant shift in the cybersecurity landscape. PwC can assist your organisation throughout the journey to NIS2 compliance.
How can we help you
With NIS2 formally adopted, entities within its scope must prepare for upcoming national transposition measures. Past experience with other regulations demonstrated that proactively addressing potential issues yields better results than attempting to correct problems after they have already arisen. Early planning allows for timely identification and prioritisation of areas needing substantial investment.
While NIS2 harmonises cybersecurity risk management and reporting requirements, many obligations align with existing regulations and standards. This allows for a proactive combined readiness assessment approach addressing the many requirements of the complex regulatory environment.
Experience and expertise
We have highly qualified specialists in the fields of information system audit, information security, legal support, and compliance.
Industry know-how
Bespoke solutions across critical and highly critical sectors.
Integrated approach
We are here to help you, from impact analysis to implementing measures.
Global network
An EMEA NIS2 network team with access across the EU and beyond, to allow cross border compliance with the directive.
By Michael Solon Kassinis, Manager, Assurance Services - Digital Trust, PwC Cyprus, PwC Cyprus
